In the previous article, we looked at the architecture of SmartLock. Now, we’ll turn our attention to its configuration, compatibility, and use.
The following CLI procedure can be used to commit a file into WORM state without having to remove the “write” permissions of end users using the chmod -w <file> command. This avoids re-enabling write permission after the files have been released from WORM retention. These commands are applicable for both Enterprise and Compliance SmartLock modes:
- Create and verify a new SmartLock domain. Note that if you specify the path of an existing directory, the directory must be empty. The following command creates an enterprise directory with a default retention period of two years, a minimum retention period of one year, and a maximum retention period of three years:.
# isi worm domains create /ifs/smartlk --default-retention 2Y --min-retention 1Y --max-retention 3Y --mkdir # isi worm domains list ID Path Type ------------------------------ 656128 /ifs/smartlk enterprise ------------------------------ Total: 1 # isi worm domains view 656128 ID: 656128 Path: /ifs/smartlk Type: enterprise LIN: 4760010888 Autocommit Offset: - Override Date: - Privileged Delete: off Default Retention: 2Y Min Retention: 1Y Max Retention: 3Y Pending Delete: False Exclusions: -
Alternatively, a WORM domain can also configured from the WebUI, by navigating to Cluster management > SmartLock and clicking on the ‘Create domain’ button:
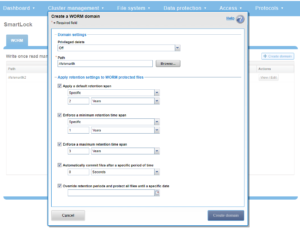
In addition to SmartLock Domains, OneFS also supports SnapRevert, SyncIQ, and writable snapshot domains. A list of all configured domains on a cluster can be viewed with the following CLI syntax:
# isi_classic domain list -l ID | Root Path | Type | Overrid | Def. | Min. | Max. | Autocomm | Priv. ---+-------------+-------------+---------+------+-------+-------+----------+------ 65>| /ifs/sync1>| SyncIQ | None | None | None | None | None | Off 65>| /ifs/smartlk>| SmartLock | None | None | None | None | None | Off 65>| /ifs/snap1| Writable,Snap>| None | None | None | None | None | Off
- Next, create a file:
# date >> /ifs/smartlk/wormfile1
- View the file’s permission bits and confirm that the owner has write permission:
# ls -lsia /ifs/smartlk
total 120 4760010888 32 drwx------ 2 root wheel 27 Feb 3 23:19 . 2 64 drwxrwxr-x + 8 root wheel 170 Feb 3 23:11 .. 4760931018 24 -rw------- 1 root wheel 29 Feb 3 23:19 wormfile1
- Examine the wormfile1 file’s contents and verify that it has not been WORM committed:
# cat /ifs/smartlk/wormfile1 cat /ifs/smartlk/wormfile1 Thu Feb 3 23:19:09 GMT 2022 # isi worm files view !$ isi worm files view /ifs/smartlk/wormfile1 WORM Domains ID Root Path ------------------- 656128 /ifs/smartlk WORM State: NOT COMMITTED Expires: -
5. Commit the file into WORM. The ‘chmod’ CLI command can be used to manually commit a file with write permission into WORM state. For example:
# chmod a-w /ifs/smartlk/wormfile1
Or:
# chmod 444 /ifs/smartlk/wormfile1
The ‘chflags’ command can also be used:
# chflags dos-readonly /ifs/smartlk/wormfile1
Similarly, a writable file can be committed from an SMB client’s GUI by checking the ‘Read-only’ attribute within the file’s ‘Properties’ tab. For example:
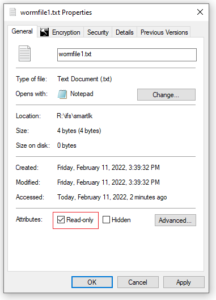
- Verify the file is committed and the permission bits are preserved:
# isi worm files view /ifs/smartlk/wormfile1 WORM Domains ID Root Path ------------------- 656128 /ifs/smartlk WORM State: COMMITTED Expires: 2024-02-03T23:23:45 # ls -lsia /ifs/smartlk total 120 4760010888 32 drwx------ 2 root wheel 27 Feb 3 23:19 . 2 64 drwxrwxr-x + 8 root wheel 170 Feb 3 23:11 .. 4760931018 24 -rw------- 1 root wheel 29 Feb 3 23:19 wormfile1
- Override the retention period expiration date for all WORM committed files in a SmartLock directory
# isi worm domains modify /ifs/smartlk --override-date 2024-08-03 # isi worm domains view 656128 ID: 656128 Path: /ifs/smartlk Type: enterprise LIN: 4760010888 Autocommit Offset: - Override Date: 2024-08-03T00:00:00 Privileged Delete: off Default Retention: 2Y Min Retention: 1Y Max Retention: 3Y Pending Delete: False Exclusions: /ifs/smartlk/wormdir1
- Create a new directory under the domain and configure it for exclusion from WORM.
# isi worm domains modify --exclude /ifs/smartlk/notwormdir1 656128
To remove an existing exclusion domain on a directory, first delete the directory and all of its constituent files.
- Verify that exclusion has been configured:
# isi worm domains view 656128 ID: 656128 Path: /ifs/smartlk Type: enterprise LIN: 4760010888 Autocommit Offset: - Override Date: - Privileged Delete: off Default Retention: 2Y Min Retention: 1Y Max Retention: 3Y Pending Delete: False Exclusions: /ifs/smartlk/notwormdir1
10: Delete the file from its enterprise WORM domain before the expiration date via the privileged delete option:
# rm -f /ifs/smartlk/wormfile1 rm: /ifs/smartlk/wormfile1: Read-only file system # isi worm files delete /ifs/smartlk/wormfile1 Are you sure? (yes/[no]): yes Operation not permitted. Please verify that privileged delete is enabled. # isi worm domains modify /ifs/smartlk --privileged-delete true # isi worm domains view /ifs/smartlk ID: 656128 Path: /ifs/smartlk Type: enterprise LIN: 4760010888 Autocommit Offset: - Override Date: 2024-08-03T00:00:00 Privileged Delete: on Default Retention: 2Y Min Retention: 1Y Max Retention: 3Y Pending Delete: False Exclusions: /ifs/smartlk/wormdir1 # isi worm files delete /ifs/smartlk/wormfile1 Are you sure? (yes/[no]): yes # ls -lsia /ifs/smartlk/wormfile1 ls: /ifs/smartlk/wormfile1: No such file or directory
- Delete SmartLock Domain.
For enterprise-mode domains, ensure the domain is empty first, then remove with ‘rmdir’:
# rmdir /ifs/smartlk/notwormdir1 # ls -lsia /ifs/smartlk total 96 4760010888 32 drwx------ 2 root wheel 0 Feb 4 00:06 . 2 64 drwxrwxr-x + 8 root wheel 170 Feb 3 23:11 .. # isi worm domains list ID Path Type ------------------------------ 656128 /ifs/smartlk enterprise ------------------------------ Total: 1 # rmdir /ifs/smartlk # isi worm domains list ID Path Type ------------ ------------ Total: 0
Note that SmartLock’s ‘pending delete’ option can only be used for compliance-mode directories:
# isi worm domains modify --set-pending-delete 656128 You have 1 warnings: Marking a domain for deletion is irreversible. Once marked for deletion:
-
No new files may be created, hardlinked or renamed into the domain.
-
Existing files may not be committed or have their retention dates extended.
-
SyncIQ will fail to sync to and from the domain.
Are you sure? (yes/[no]): yes Cannot mark non-compliance domains for deletion.
In the following table, the directory default retention offset is configured for one year for both scenarios A & B. This means that any file committed to that directory without a specific expiry date (ie. scenario A) will automatically inherit a one year expiry from the date it’s committed. As such, WORM protection for any files committed on 2/1/2022 will be until 2/1/2023, based on the default one year setting. In scenarios A & B, the retention date of 3/1/2023 takes precedent over any directory default retention offset period. In scenario D, the Override Retention Date, configured at the directory level, ensures that all data in that directory is automatically protected through a minimum of 1/31/2023. This can be useful for organizations to satisfy litigation holds and other blanket data retention requirements.
| Scenario A
No file-retention date |
Scenario B
File-retention date > directory offset |
Scenario C
Directory-offset > file-retention date |
Scenario 4
Override retention date |
|
| File-retention date | N/A | 3/1/2023 | 3/1/2023 | 3/1/2023 |
| Directory-offset retention date | 1 year | 1 year | 2 years | 1 year |
| File-committed date | 2/1/2022 | 2/1/2022 | 2/1/2022 | 2/1/2022 |
| Expiration date | 2/1/2023 | 3/1/2023 | 3/1/2023 | 1/31/2023 |
In general, SmartLock plays nicely with OneFS and the other data services. For example, SnapshotIQ can take snaps of data in a WORM directory. Similarly, SmartLock retention settings are retained aross NDMP backups, avoiding the need to recommit files after a data restore. Be aware, though, that NDMP backups of SmartLock Compliance data do not satisfy the regulatory requirements of SEC 17a-4(f).
For CloudPools, WORM protection of SmartLink stub files is permitted in OneFS 8.2 and later, but only in Enterprise mode. Stubs can be moved into an Enterprise mode directory, preventing their modification or deletion, as well as recalled from the cloud to the cluster once committed.
SyncIQ interop with SmartLock has more complexity, context, and caveats, and the compatibility between different directory types on the replication source and target can be characterized as follows:
| Source dir | Target dir | SyncIQ failover | SyncIQ failback |
| Non-WORM | Non-worm | Yes | Yes, unless files are WORM committed on target. Retention not enforced. |
| Non-WORM | Enterprise | Yes | No |
| Non-WORM | Compliance | No | Yes: But files do not have WORM status. |
| Enterprise | Non-worm | Yes: Replication type allowed, but retention not enforced | Yes: Newly committed WORM files included. |
| Enterprise | Enterprise | Yes | No |
| Enterprise | Compliance | No | No |
| Compliance | Non-worm | No | No |
| Compliance | Enterprise | No | No |
| Compliance | Compliance | Yes | Yes: Newly committed WORM files are included |
When using SmartLock with SyncIQ replication, configure Network Time Protocol (NTP) peer mode on both the source and target cluster to ensure that cluster clocks are synchronized. Where possible, also run the same OneFS version across replication pairs and create a separate SyncIQ policy for each SmartLock directory.