Among the array of HTTP services, and in addition to the platform API, OneFS also provides a namespace API.
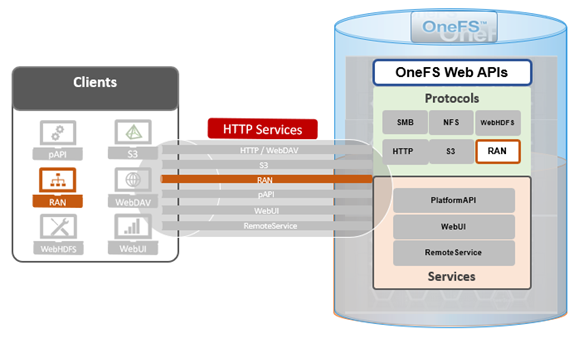
This RESTful Access to Namespace, or RAN, provides HTTP access to any of the files and directories within a cluster’s /ifs filesystem hierarchy.
RAN can be accessed by making an HTTP call that references the /namespace/ API, rather than the /platform/ API that we’ve seen in the previous articles in this series. For example:
namespace == “http share”
This provides HTTPS access to the files & directories on the filesystem, but more as a data management API rather than object.
As you would expect, by default, the root of a cluster’s RAN namespace is the top level /ifs directory:
Namespace resources are accessed through a URL, such as:
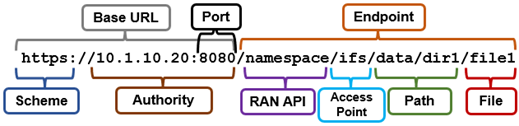
Where:
| Attribute | Description |
| Access point | Access Point is the root path of the file system endpoint (RAN share), ie. /ifs. |
| Authority | Authority is the IP address or FQDN for the cluster. |
| Container | Container is a directory or folder. |
| Data object | Data object contains content data, such as a file on the system. |
| Endpoint | Endpoint is the targetable URL. |
| File | File is the data object you wish to query/modify. |
| Namespace | Namespace is the file system structure on the cluster. |
| Object | Object is either a container or data object. |
| Path | Path is the file path to the object you want to access. |
| Port | Port is the number of the port; the default port number is 8080 |
| Scheme | Scheme is the access protocol method |
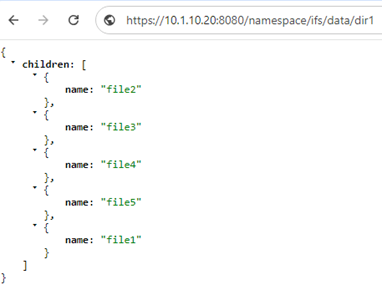
For example, using the RAN API to access the file ‘file1’ which resides in the ‘dir1’ directory under the access point and path ‘/ifs/data/dir1/’.
From the OneFS CLI, the ‘curl’ utility can be used to craft a ‘GET’ request for this file:
# curl -u <user:password> -k https://10.1.10.20:8080/namespace/ifs/data/dir1/file1
Or from a browser:
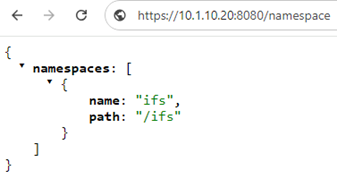
Also, using ‘curl’ via the CLI to view the RAN access point:
# curl -X GET https://10.1.10.20:8080/namespace --insecure --basic --user root:a
{"namespaces":[{
"name" : "ifs",
"path" : "/ifs"
}
]}#
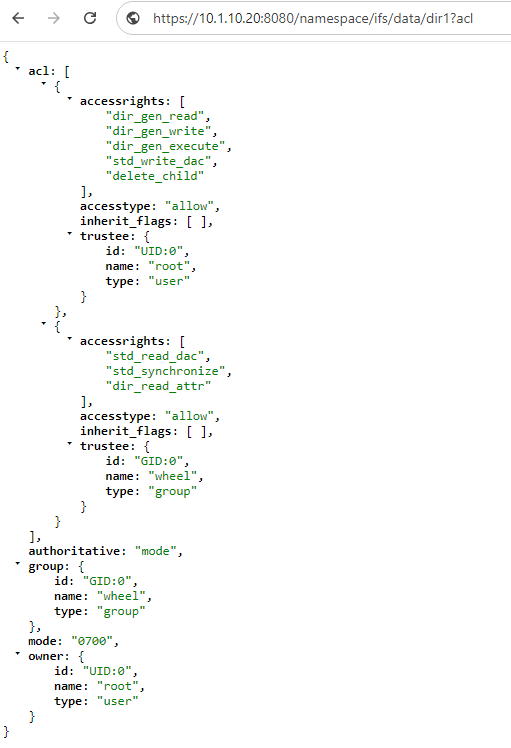
Additionally, you can append a pre-defined keyword to the end of the URL when you send a request to the namespace. These keywords must be placed first in the argument list and must not contain any value. If these keywords are placed in any other position in the argument list, the keywords are ignored. Pre-defined keywords include: ‘acl’, ‘metadata’, ‘worm’, and ‘query’.
For example:
https://10.1.10.20:8080/namespace/ifs/data/dir1?acl
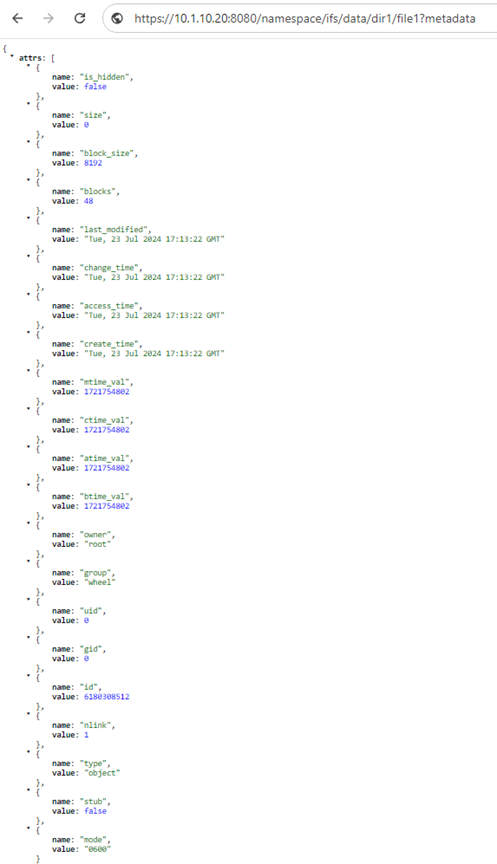
Or for metadata. For example:
https://10.1.10.20:8080/namespace/ifs/data/dir1/file1?metadata
A cluster’s files and directories can be accessed programmatically through RAN, similarly to the way they’re accessed through SMB or NFS protocols, as well as limited by filesystem permissions. As such RAN enables the following types of file system operations to be performed.
| Operation | Action | Description |
| Access points | CREATE, DELETE | Identify and configure access points (shares) and obtain protocol information. |
| Directory | CREATE, GET, PUT, LIST, DELETE | List directory content.; get and set directory attributes; delete directories from the file system. |
| File | CREATE, GET, PUT, LIST, DELETE | View, move, copy, and delete files from the file system. |
| Access control | GET/SET ACLs | Manage user rights; set ACL or POSIX permissions for files and directories. Set access list on access points (RAN Share Permissions). |
| Query | QUERY
|
Search system metadata or extended attributes, and tag files. |
| SmartLock | GET, SET, Commit | Allow retention dates to be set on files; commit files to a WORM state. |
Additionally, applications or external clients can be built to access RAN in any major programming or scripting language, such as C++, Java, .net, Python, etc.
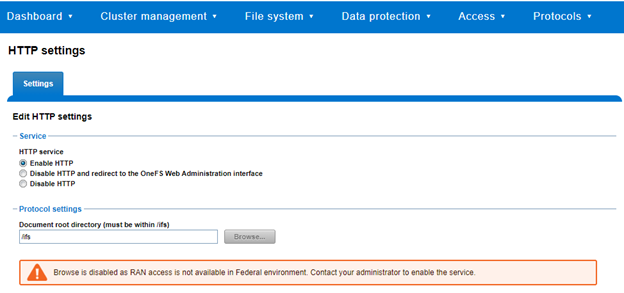
Note, though, that RAN access in general is disabled for clusters running in ‘hardened’ mode. In such cases a warning will be displayed notifying that HTTP browse is disabled, similar to the following: