Data-at-rest data is inactive content that is physically housed on a cluster, or other storage medium. Protecting this data with cryptography ensures that it’s guarded against theft, in the event that drives or nodes are removed from a PowerScale cluster. Data-at-rest encryption (DARE) is a requirement for federal and industry regulations ensuring data is encrypted when it is stored. OneFS has provided DARE solutions for many years through self-encrypting drives (SEDs) and, until now, an internal key management system.
The new OneFS 9.2 release introduces External Key Management (EKM) support for encrypted clusters, through the key management interoperability protocol, or KMIP. This enables offloading of the Master Key from a node to an External Key Manager, such as SKLM, SafeNet or Vormetric. Enhanced security is inherently provided through the separation of key manager from cluster, since node(s) cannot be rebooted without the keys. It also supports the secure transport of nodes. Additionally, centralized key management is also made available for multiple SED clusters, and provides the option to migrate existing keys from a cluster’s internal key store.
EKM provides enhanced security through the separation of the key manager from the cluster, enabling the secure transport of nodes, and helping organizations to meet regulatory compliance and corporate data at rest security requirements.
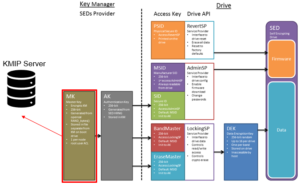
In order to use the OneFS 9.2 External Key Manager feature, clearly a cluster with self-encrypting drives is needed. Additionally, for the SED drives to be unlocked and user data made available, each node in the cluster must first contact the KMIP server to obtain the master encryption key from the server. Nodes in the cluster cannot boot without contacting the KMIP server first. Note that clusters without all their nodes connected to a front-end network (NANON) do not support External Key Management.
For the server, a KMIP Compliant Server supporting KMIP version 1.2 or greater is needed, such as:
| Vendor | Key Manager & Version |
| Dell EMC | CloudLink Center 6.0 |
| Gemalto | Gemalto KeySecure 8.7 k150v
Gemalto KeySecure 8.7 k170v |
| IBM | Secure Key Lifecycle Manager (SKLM) 2.6.0.2
Secure Key Lifecycle Manager (SKLM) 2.7.0.0 Secure Key Lifecycle Manager (SKLM) 3.0.0 |
| Thales | E-Security KeyAuthority 4.0 |
Also:
- KMIP Storage Array with SEDS Profile Version 1.0
- KMIP server host/port information
- 509 PKI for TLS mutual authentication
- Certificate authority bundle
- Client certificate and private key
External Key Management can be configured on OneFS 9.2 as follows:
- Obtain the KMIPs Server and Client Certificates. Copy both certificates to the cluster and make a note of the file names and location.
- From the OneFS web interface, select Access > Key Management
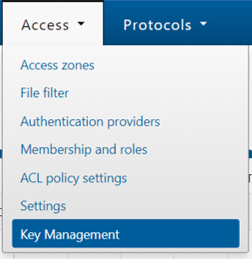
Alternatively, this can also be accomplished via the OneFS CLI:
# isi keymanager kmip servers create
- From the WebUI Key Management page, enter the KMIP server information and specify the filename with the server/client certificates’ location. If the KMIP has a client certificate password specified, enter that here. Check the “Enable Key Management” box and click Submit.
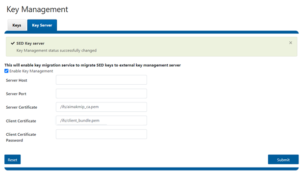
- Next, OneFS contacts the KMIP and confirms the connection or displays any errors.
- Once the KMIP server is added, the keys can now be migrated. Click the Keys tab to display all current Master Keys on the cluster. Click on Migrate all to migrate the keys to the KMIP server. From the “Migrate all” pop-up, click Migrate to start the migration.
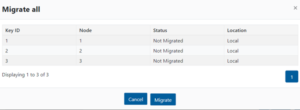
- The key migration process may take several minutes or more to complete depending on the cluster and network utilization. During this time, a “Migration in process” message is displayed.
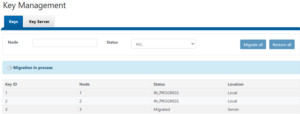
- Once the process is complete, and “Migration Successful” message is displayed:
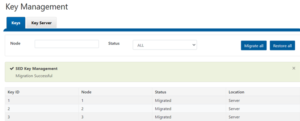
The following OneFS key management CLI commands are also available:
To configure external KMIP servers:
# isi keymanager kmip servers -h
Description:
Configure external KMIP servers.
Required Privileges:
ISI_PRIV_KEY_MANAGER
Usage:
isi keymanager kmip servers <action>
[--timeout <integer>]
[{--help | -h}]
Actions:
create Configure a new external KMIP server.
delete Delete a external KMIP server.
modify Modify a external KMIP server.
list View a list of configured external KMIP servers.
view View a single external KMIP server.
Options:
Display Options:
--timeout <integer>
Number of seconds for a command timeout (specified as 'isi --timeout NNN <command>').
--help | -h
Display help for this command.
See 'isi keymanager kmip servers <subcommand> --help' for more information on a specific subcommand.
To manage SED keystore settings:
# isi keymanager sed settings -h
Description:
Manage self-encrypting drive keystore settings.
Required Privileges:
ISI_PRIV_KEY_MANAGER
Usage:
isi keymanager sed settings <action>
[{--help | -h}]
Actions:
modify Modify SED settings
view View current SED settings.
Options:
Display Options:
--help | -h
Display help for this command.
See 'isi keymanager sed settings <subcommand> --help' for more information on a specific subcommand.
And to report keymanager SED status:
# isi keymanager sed status Node Status Location Remote Key ID Error Info(if any) ---------------------------------------------------------- 1 REMOTE Server F84B50640CABD44B9D5F75427C2B5E 2 REMOTE Server 24285969BD8804A9A61EE39D99573B 3 REMOTE Server 7D561B1CA89B72B891B21BF834097F ----------------------------------------------------------- Total: 3