Unlike previous OneFS versions, SyncIQ is disabled by default in OneFS 9.1 and later. Once SyncIQ has been enabled by the cluster admin, a global encryption flag is automatically set, requiring all SyncIQ policies to be encrypted. Similarly, when upgrading a PowerScale cluster to OneFS 9.1, the global encryption flag is also set. However, be aware that the global encryption flag is not enabled on clusters configured with any existing SyncIQ policies upon upgrade to OneFS 9.1 or later releases.
The following procedure can be used to configure SyncIQ encryption from the OneFS CLI:
- Ensure both source and target clusters are running OneFS 8.2 or later.
- Next, create an X.509 certificates, one for each of the source and target clusters, and signed by a certificate authority.
| Certificate Type | Abbreviation |
| Certificate Authority | <ca_cert_id> |
| Source Cluster Certificate | <src_cert_id> |
| Target Cluster Certificate | <tgt_cert_id> |
These can be generated using publicly available tools, such as OpenSSL: http://slproweb.com/products/Win32OpenSSL.html.
- Add the newly created certificates to the appropriate source cluster stores. Each cluster gets certificate authority, its own certificate, and its peer’s certificate:
# isi sync certificates server import <src_cert_id> <src_key> # isi sync certificates peer import <tgt_cert_id> # isi cert authority import <ca_cert_id>
- On the source cluster, set the SyncIQ cluster certificate:
# isi sync settings modify --cluster-certificate-id=<src_cert_id>
- Add the certificates to the appropriate target cluster stores:
# isi sync certificates server import <tgt_cert_id> <tgt_key> # isi sync certificates peer import <src_cert_id> # isi cert authority import <ca_cert_id>
- On the target cluster, set the SyncIQ cluster certificate:
# isi sync settings modify --cluster-certificate-id=<tgt_cert_id>
- A global option is available in OneFS 9.1, requiring that all incoming and outgoing SyncIQ policies are encrypted. Be aware that executing this command impacts any existing SyncIQ policies that may not have encryption enabled. Only execute this command once all existing policies have encryption enabled. Otherwise, existing policies that do not have encryption enabled will fail. To enable this, execute the following command:
# isi sync settings modify --encryption-required=True
- On the source cluster, create an encrypted SyncIQ policy:
# isi sync policies create <pol_name> sync <src_dir> <target_ip> <tgt_dir> --target-certificate-id=<tgt_cert_id>
Or modify an existing policy on the source cluster:
# isi sync policies modify <pol_name> --target-certificate-id=<tgt_cert_id>
OneFS 9.1 also facilitates SyncIQ encryption configuration via the OneFS WebUI, in addition to CLI. For the source, server certificates can be added and managed by navigating to Data Protection > SyncIQ > Settlings and clicking on the ‘add certificate’ button:
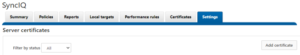
And certificates can be imported onto the target cluster by browsing to Data Protection > SyncIQ > Certificates and clicking on the ‘add certificate’ button. For example:
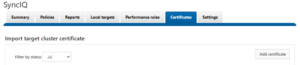
So that’s what’s required to get encryption configured across a pair of clusters. There are several addition optional encryption configuration parameters available. These include:
- Updating the policy to use a specified SSL cipher suite:
# isi sync policies modify <pol_name> --encryption-cipher-list=<suite>
- Configuring the target cluster to check the revocation status of incoming certificates:
# isi sync settings modify --ocsp-address=<address> --ocsp-issuer-certificate-id=<ca_cert_id>
- Modifying how frequently encrypted connections are renegotiated on a cluster:
# isi sync settings modify --renegotiation-period=24H
- Requiring that all incoming and outgoing SyncIQ policies are encrypted:
# isi sync settings modify --encryption-required=True
To troubleshoot SyncIQ encryption, first check the reports for the SyncIQ policy in question. The reason for the failure should be indicated in the report. If the issue was due to a TLS authentication failure, then the error message from the TLS library will also be provided in the report. Also, more detailed information can often be found in /var/log/messages on the source and target clusters, including:
- ID of the certificate that caused the failure.
- Subject name of the certificate that caused the failure.
- Depth at which the failure occurred in the certificate chain.
- Error code and reason for the failure.
Before enabling SyncIQ encryption, be aware of the potential performance implications. While encryption only adds minimal overhead to the transmission, it may still negatively impact a production workflow. Be sure to test encrypted replication in a lab environment that emulates the environment before deploying in production.
Note that both the source and target cluster must be upgraded and committed to OneFS 8.2 or later, prior to configuring SyncIQ encryption.
In the event that SyncIQ encryption needs to be disabled, be aware that this can only be performed via the CLI and not the WebUI:
# isi sync settings modify --encryption-required=false
If encryption is disabled under OneFS 9.1, the following warnings will be displayed on creating a SyncIQ policy.
From the WebUI:
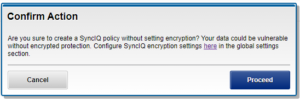
And via the CLI:
# isi sync policies create pol2 sync /ifs/data 192.168.1.2 /ifs/data/pol1 ******************************************** WARNING: Creating a policy without encryption is dangerous. Are you sure you want to create a SyncIQ policy without setting encryption? Your data could be vulnerable without encrypted protection. Type ‘confirm create policy’ to proceed. Press enter to cancel: